Introduction
The world of cybersecurity is constantly evolving, and new threats are emerging every day. One such threat is the NoFilter Attack, which has recently been discovered as a silent Windows security nightmare. In this article, we will delve into the details of this attack and discuss why it is crucial to prioritize Windows security.
Table of Contents
Key Takeaways
- The NoFilter Attack is a silent Windows security nightmare that exploits vulnerabilities in the Windows Filtering Platform (WFP) to achieve privilege escalation and gain unauthorized access to SYSTEM privileges.
- Understanding how WFP works and its role in processing network traffic is crucial in protecting against attacks like NoFilter.
- NoFilter is an evasive attack that leaves minimal evidence or logs, making it difficult to detect or track.
- To mitigate the risks associated with attacks like NoFilter, organizations should prioritize proactive security measures such as regular updates, strong access controls, and advanced threat detection solutions.
- Staying informed about emerging threats and vulnerabilities is essential for maintaining a robust cybersecurity posture and protecting sensitive data and systems. [1][2]
Overview of the NoFilter Attack
The NoFilter Attack exploits the Windows Filtering Platform (WFP) to achieve privilege escalation in the Windows operating system. It takes advantage of an in-house tool called RPC Mapper to map remote procedure call (RPC) methods and discover a method named “BfeRpcOpenToken” within WFP. By retrieving the handle table of another process, the attacker can duplicate the handles to escalate their privileges to SYSTEM level.
What makes this attack particularly dangerous is its evasive nature. By performing the duplication in the kernel through WFP, it leaves behind minimal evidence or logs, making it difficult to detect or track. This enables attackers to launch a new console as NT AUTHORITY SYSTEM or as another logged-in user without raising suspicion.
Importance of Windows Security
Windows security plays a crucial role in protecting sensitive data and preventing unauthorized access. With cyber threats becoming increasingly sophisticated, it is essential for individuals and organizations to prioritize Windows security measures. Regular updates, strong passwords, and vigilant user behavior are just a few examples of key practices that can enhance Windows security.
By staying proactive and implementing robust security measures, individuals and businesses can fortify their systems against attacks like NoFilter. Investing in reliable antivirus software, practicing safe browsing habits, and regularly backing up data are also effective strategies for maintaining Windows security.
In conclusion, understanding the NoFilter Attack and its implications highlights the importance of prioritizing Windows security. By adopting robust security measures and staying informed about emerging threats, individuals and organizations can better protect their Windows systems from potential breaches and ensure the safety of their valuable data. [1][2][3][4]
Understanding the Windows Filtering Platform (WFP)
In the world of cybersecurity, new threats are constantly emerging, and the NoFilter Attack is one that has recently come to light. This attack exploits a vulnerability in the Windows Filtering Platform (WFP) to escalate privileges in the Windows operating system. Understanding how WFP works is crucial in protecting against such attacks.
Explaining the role of WFP in processing network traffic
WFP is a set of APIs and system services that provide a platform for creating network filtering applications. It allows for the processing of network traffic at various layers of the networking stack in the operating system. By intercepting and inspecting network packets, WFP enables the implementation of filters that can permit or block communications based on specific criteria.
How WFP allows configuring filters for communication
One of the key functionalities of WFP is its ability to configure filters for communication. These filters can be defined based on various parameters, such as source and destination IP addresses, ports, protocols, and even specific application traffic. By defining these filters, organizations can control and monitor network traffic, ensuring that only authorized communications are allowed.
However, it is important to note that attackers can exploit vulnerabilities in WFP to bypass these filters and escalate their privileges within the operating system. The NoFilter Attack is one such example, where an attacker gains admin-level access and then exploits WFP to escalate their privileges to SYSTEM level.
To mitigate the risks associated with such attacks, organizations should stay vigilant in keeping their systems up to date with the latest security patches. Additionally, implementing defense-in-depth strategies that combine multiple security measures can help detect and prevent attacks targeting WFP.
In conclusion, understanding the Windows Filtering Platform and its vulnerabilities is crucial in protecting against cyber threats like the NoFilter Attack. By staying informed and implementing robust security measures, organizations can ensure the safety and integrity of their Windows-based systems. [5][6][7][8]
The Discovery of BfeRpcOpenToken
The cybersecurity world has been rocked by the unveiling of a new attack method known as NoFilter. This silent nightmare bypasses Windows security to achieve privilege escalation in the operating system. The discovery of this attack was presented at the DEF CON security conference, and it has shed light on a vulnerability that many were previously unaware of.
Introduction to RPC Mapper and its role in the discovery
The journey towards uncovering NoFilter began with the use of an in-house tool called RPC Mapper. This tool was employed by a cybersecurity company to map remote procedure call (RPC) methods, specifically those that invoke the Windows Filtering Platform (WFP). Through this exploration, a method named BfeRpcOpenToken was discovered, which is part of WFP.
Exploring the BfeRpcOpenToken method in WFP
The WFP is a crucial component used to process network traffic and configure filters that permit or block communications. By calling NtQueryInformationProcess and retrieving the handle table of another process, researchers were able to access tokens held by the process. These tokens could then be duplicated for another process to escalate privileges to SYSTEM level.
NoFilter is a stealthy attack that leaves minimal evidence or logs, making it difficult to detect. It emphasizes the importance of scrutinizing built-in components of an operating system, such as WFP, in order to uncover potential vulnerabilities. This discovery serves as a reminder for organizations to prioritize cybersecurity measures and stay vigilant against evolving threats. [9][10][11][12]
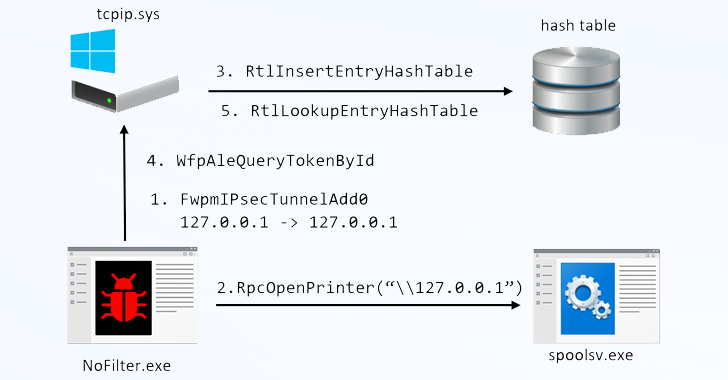
Privilege Escalation from Admin to SYSTEM
In the world of cybersecurity, new attack methods are constantly emerging, and the latest one to cause concern is the NoFilter Attack. This silent Windows security nightmare exploits a vulnerability in the Windows Filtering Platform (WFP) to achieve privilege escalation from admin to SYSTEM.
Explanation of the handle table and token duplication
To understand how this attack works, it’s important to delve into the technical details. The handle table of a process contains the tokens that determine the privileges of that process. By duplicating these tokens, an attacker can escalate their privileges and gain elevated access.
In the case of the NoFilter Attack, a method called BfeRpcOpenToken, discovered within WFP, is used to retrieve the handle table of another process. Using specific functions like DuplicateToken or DuplicateHandle, the attacker can duplicate these tokens for another process and escalate their privileges to SYSTEM.
How the NoFilter Attack can escalate privileges
With their new elevated privileges, the attacker can carry out malicious activities undetected. They can launch a new console as NT AUTHORITYSYSTEM or even impersonate another user who is logged onto the targeted machine.
This attack method is particularly concerning because it bypasses common security monitoring techniques by exploiting built-in components like WFP. It leaves little evidence or logs behind, making it a stealthy and evasive threat.
As cybersecurity professionals continue to combat evolving threats, understanding and staying informed about attacks like the NoFilter Attack are crucial for protecting sensitive data and systems. Being vigilant and implementing robust security measures is essential in defending against such silent nightmares. [13][14][15][16]
Unveiling NoFilter Attack: A Silent Windows Security Nightmare (Part 1)
A new method of attack called NoFilter has recently been discovered, revealing a silent Windows security nightmare. This attack leverages the Windows Filtering Platform (WFP) to achieve privilege escalation in the Windows operating system. It was presented at the DEF CON security conference, shedding light on the potential vulnerabilities that businesses need to be aware of.
Evasion and Stealth Techniques
The NoFilter attack starts with an in-house tool called RPC Mapper, which is used to map remote procedure call (RPC) methods. This exploration led to the discovery of a method named BfeRpcOpenToken, which is part of the WFP. By retrieving the handle table of another process and duplicating the tokens held by that process, an attacker can escalate their privileges from admin to SYSTEM level.
Modifying the technique to perform duplication in the kernel
What makes NoFilter particularly troublesome is its ability to modify the technique to perform duplication in the kernel via WFP. This modification makes the attack evasive and stealthy, leaving behind minimal evidence or logs. Attackers can launch new consoles as NT AUTHORITY SYSTEM or as another user logged onto the machine.
Benefits of evasive and stealthy attacks
The evasive and stealthy nature of the NoFilter attack poses a significant threat to businesses. By bypassing traditional security measures, attackers can encrypt files without executing code, neutralize endpoint detection and response agents, and remotely delete entire databases. With these capabilities, cybercriminals can go undetected and wreak havoc on an organization’s systems.
In conclusion, understanding and addressing vulnerabilities like the NoFilter attack is crucial for businesses’ cybersecurity strategies. By staying informed about emerging threats and implementing effective security measures, organizations can better protect their networks from these silent nightmares. [17][18][19][20]
Unveiling NoFilter Attack: A Silent Windows Security Nightmare (Part 2)
The cybersecurity world has been shaken by the discovery of a new attack method called NoFilter. This attack has the potential to bypass Windows security measures and achieve privilege escalation within the Windows operating system.
Implications and Potential Attack Vectors
NoFilter Attack takes advantage of the Windows Filtering Platform (WFP), which is a system used to process network traffic and configure filters. By exploring built-in OS components like WFP, attackers can find new attack vectors that can be exploited. This makes it crucial for organizations to understand and mitigate these risks.
Expanding the attack surface by avoiding WinAPI
One of the most alarming aspects of NoFilter Attack is its ability to bypass security product monitoring by avoiding commonly monitored Windows API (WinAPI) calls. This evasion technique allows attackers to remain undetected while launching their malicious activities.
To protect against this silent nightmare, organizations must invest in comprehensive security measures that go beyond traditional methods. This includes implementing strong access controls, regularly updating security patches, and monitoring their systems for any suspicious activities.
It is also essential for organizations to keep themselves informed about the latest cybersecurity threats and vulnerabilities. By staying ahead of the game and proactively addressing potential attack vectors, businesses can better safeguard their sensitive data and maintain a secure operating environment.
In conclusion, NoFilter Attack serves as a wakeup call for businesses to reevaluate their security strategies and ensure they are equipped to defend against evolving cyber threats. By exploring all potential attack vectors and avoiding common monitoring techniques, organizations can stay one step ahead of attackers and protect their valuable assets. [21][22][23][24]

Similar Attacks and Security Concerns
In the world of cybersecurity, new threats and vulnerabilities are constantly emerging. One such silent security nightmare is the NoFilter attack. This attack has been found to bypass Windows security and escalate privileges, potentially leading to serious consequences for organizations running a Windows operating system.
Discussion on other attacks exploiting Windows vulnerabilities
The NoFilter attack method exploits the Windows Filtering Platform (WFP), which is commonly used to configure filters and process network traffic. By mapping remote procedure call (RPC) methods and invoking WinAPI, attackers can reach BfeRpcOpenToken, a part of the WFP. This allows them to retrieve access tokens that can be duplicated to escalate from admin to SYSTEM privileges.
This new method of attack is significant because it bypasses the protection provided by the WFP against attacks like LSASS Shtinkering. The attack can go undetected in logs, making it difficult for organizations to detect and track.
This attack highlights the importance of scrutinizing built-in components in an operating system for potential vulnerabilities. It also emphasizes the need for strong proactive security measures to prevent such attacks.
The need for proactive security measures
To protect against attacks like NoFilter, organizations need to adopt proactive security measures. Proactive cybersecurity involves identifying and patching vulnerabilities, regularly evaluating security posture, and implementing strong access controls and authentication measures. It also includes continuous monitoring for emerging threats and updating security measures accordingly.
By taking a proactive approach to security, organizations can stay one step ahead of attackers and significantly reduce the risk of breaches and data compromise. Implementing robust security measures not only protects valuable data but also helps build trust with customers and stakeholders.
In conclusion, the NoFilter attack serves as a reminder of the constant need for vigilance in the ever-evolving world of cybersecurity. Organizations must be proactive in their security efforts to effectively defend against emerging threats and protect their systems, data, and reputation. [25][26][27][28]
Mitigation and Defense Strategies
The recent discovery of the NoFilter attack has unveiled a silent Windows security nightmare that could potentially lead to privilege escalation in the Windows operating system. This attack takes advantage of the Windows Filtering Platform (WFP) and can bypass Windows security measures, making it difficult to detect.
To protect against this attack, it is important for users and organizations to implement the following defense strategies:
Recommendations for protecting against the NoFilter Attack
- Regularly update and patch: Keeping your operating system and security software up-to-date is crucial to mitigating the risks associated with new vulnerabilities. Regular updates and patches help ensure that your system is equipped with the latest security measures.
- Implement strong access controls: Limiting admin privileges and implementing robust access controls can help prevent attackers from escalating their privileges and gaining unauthorized access to sensitive information.
- Employ application whitelisting: Implementing application whitelisting can help protect against unauthorized applications from running on your system, limiting the attack surface for potential threats.
- Utilize advanced threat detection solutions: Deploying advanced threat detection solutions, such as endpoint protection platforms and intrusion detection systems, can help identify suspicious activities and potential attacks.
Importance of regular updates and patches
Regularly updating and patching your software is crucial to maintaining a secure environment. Updates not only add new features but also fix bugs and vulnerabilities that attackers might exploit. By staying up-to-date with the latest patches, you can ensure that your system is protected against known vulnerabilities.
In conclusion, protecting against the NoFilter attack requires a multi-layered approach, including regular updates, strong access controls, application whitelisting, and advanced threat detection solutions. By following these recommendations, users and organizations can enhance their security posture and mitigate the risks associated with this silent Windows security nightmare. [29][30][31][32]
FAQ’s
| Question | Answer |
|---|---|
| What is a privilege escalation method? | A privilege escalation method is a technique used by attackers to gain higher levels of access or privileges that they originally had on a system. This allows them to access restricted information, execute unauthorized commands, and potentially compromise the security of the system. |
| How does a privilege escalation method bypass Windows security? | Privilege escalation methods bypass Windows security by exploiting vulnerabilities or weaknesses in the operating system or its applications. Attackers may take advantage of misconfigurations, software bugs, or insecure settings to elevate their privileges and gain unauthorized access to sensitive resources. |
| What is the Windows Filtering Platform (WFP)? | The Windows Filtering Platform (WFP) is a network security component in the Windows operating system. It provides a framework for implementing network packet filtering, firewall, and intrusion detection functionalities. WFP operates at the network and transport layers, allowing for efficient filtering and monitoring of network traffic. |
| Can you explain the concept of “no-filter” attacks? | In “no-filter” attacks, attackers exploit vulnerabilities within network infrastructure or systems to bypass or disable network filtering mechanisms. By doing so, they can evade detection, manipulate traffic, or gain unauthorized access to network resources. “No-filter” attacks often involve techniques like firewall evasion, traffic manipulation, or exploiting weaknesses in network device configurations. |
| How can an attacker achieve privilege escalation in the Windows operating system? | An attacker can achieve privilege escalation in the Windows operating system by exploiting vulnerabilities, such as unpatched software, weak user account permissions, insecure configurations, or using malicious software. Once a vulnerability is exploited, the attacker may gain more privileges, allowing them to access sensitive data, execute malicious code, or take control of the system. Regularly applying security patches and maintaining strong access controls help mitigate privilege escalation risks. |
Conclusion
The NoFilter attack has unveiled a silent nightmare in Windows security, highlighting the vulnerabilities in the Windows Filtering Platform (WFP) and the potential for privilege escalation. This attack method bypasses conventional security measures and allows for unauthorized access to SYSTEM privileges.
Recap of the NoFilter Attack and its impact on Windows security
In the NoFilter attack, the WFP is exploited by mapping remote procedure call (RPC) methods to reach a specific component called BfeRpcOpenToken. By retrieving the handle table of a Windows process, access tokens can be duplicated to escalate privileges from admin to SYSTEM level. This technique is evasive and leaves minimal evidence or logs, making it difficult to detect and track.
Importance of staying vigilant and proactive in cybersecurity
The NoFilter attack serves as a reminder of the ever-evolving threat landscape and the need for businesses and individuals to stay vigilant and proactive in their cybersecurity practices. Regularly updating security measures, implementing strong access controls, patching vulnerabilities promptly, and staying informed about emerging threats are all critical steps to protect against attacks like NoFilter.
It is crucial to leverage built-in components such as the WFP but also complement them with third-party security solutions to ensure comprehensive protection. By taking a proactive approach to cybersecurity, businesses can better anticipate and prevent attacks before they occur.
In conclusion, the NoFilter attack highlights the importance of continuous monitoring, updating, and strengthening of security measures to defend against evolving threats. By staying informed, implementing best practices, and investing in robust cybersecurity solutions, businesses can mitigate risks and safeguard their systems and data from potential attacks. [33][34][35][36]

